Browser extensions put millions of Google Chrome users at risk

Browser extensions can be an excellent way to increase their productivity while sailing. Chrome, which is the most popular browser, admits a wide range of extensions, and also other chrome -based browsers. However, these extensions are not always beneficial. While many are useful for blocking ads, finding the best offers or verifying grammar errors, some may end up doing more damage than well.
I recently informed about a group of malicious extensions They were stealing user data, and now a new report has marked 35 more suspicious. These browser extensions request unnecessary permits and it has been reported that they collect and share everything online.
Usa to the “Cyberguy Free Report: Obtain my expert technical advice, critical security alerts and exclusive offers, in addition to instant access to my free “Survival guide for definitive scam “ When you register!

A man who uses Google Chrome browser on his laptop. (Kurt “Cyberguy” Knutsson)
Incomplete extensions in nature
A recent one John Tuckner researchFounder of Secure Annex, revealed concerns about 35 chrome extensions, which raises possible risks of privacy and security. These extensions, many not listed in the Chrome web store, were installed collectively more than 4 million times.
Many of these incomplete extensions were presented as tools for search assistance, advertisement blocking, security monitoring or extension scan, but shared a connection with a unique and unused domain, which suggests coordinated behavior. All use the same code patterns, connect to some of the same servers and require the same list of confidential systems permits, including the ability to interact with web traffic in all the URLs visited, access cookies, manage browser tabs and run scripts.
What is more worrying is that at least 10 of these extensions carried Google’s “outstanding” badge, which implies a trusted investigation. This raises questions about Google’s review process, since the badge suggests compliance with high standards for user experience, privacy and security.

A hacker at work. (Kurt “Cyberguy” Knutsson)
How to stay unknown and hide your number by calling someone
Why are these extensions bad?
The main concern is the level of access that these extensions request silently and how they use it. With permissions to read tabs, access cookies, interception and injecting web applications in pages, they can monitor almost everything he does in their browser. This includes tracking your navigation activity, observing login sessions and altering the content of the websites that visit, all without your knowledge.
These extensions are not simply poorly configured tools. They seem to be intentionally designed with surveillance in mind. Many store their configuration data locally, allowing remote servers to update their behavior at any time. This configuration is commonly seen in Spyware, where changes can be made after installation without alerting the user. The code is very obfuscated, which makes it difficult for researchers to understand what extensions are really doing.
In some cases, extensions seem to do nothing when clicking. However, they continue to send data in the background. For example, the protection of the extension of the fire shield remained inactive until the researcher manually activated it with a specific extension ID. Only then began to transmit the navigation activity and other data, revealing a behavior that would be difficult for an average detect user.

A person who works on his laptop. (Kurt “Cyberguy” Knutsson)
Malware exposes 3.9 billion passwords in a great threat of cybersecurity
The 35 extensions to eliminate right now
The 35 extensions cannot be publicly sought at the Chrome web store, which means that they can only be installed through direct URLs. The full list of extensions is:
- Choose your Chrome tools
- Saféz of fire shield chrome
- Sure search for Chrome
- Fire shield extension protection
- Chrome browser review by the doctor
- Chrome protein
- Impartial search for protoo
- Assurance of your browser
- Web Privacy Assistant
- Kids Surify protection
- Bing Surify search
- Sure explore for Chrome
- Better navigate for Securitysearch
- Check my permits for Chrome
- Chrome website security
- Multisearch for Chrome
- Global Chrome Search
- Chrome maps search
- Look at the tower description
- Incognito shield for Chrome
- On the site search for Chrome
- Chrome Privacy Guard
- Yahoo search for ghost
- Chrome private search
- Total security for Chrome
- Data shield for Chrome
- Browser Watchdog for Chrome
- Chrome incognito search
- Web results for chrome
- Cuponomy – coupon and reimbursement
- Surify for Chrome
- Solution advanced web protection
- News search for Chrome
- Securitybrowse for Chrome
- Sure explore for Chrome
How to delete a Google Chrome extension on the desktop
If you have installed one of the extensions mentioned above in your browser, check it out as soon as possible. To eliminate an extension of Google Chrome on a desk, follow these steps:
- Open chrome and click on the icon that looks like a piece of puzzle. You will find it in the upper right corner of the browser
- You can see all active extensions now. Click on the three -point icon next to the extension you want to eliminate and select Remove from Chrome
- Click Eliminate To confirm
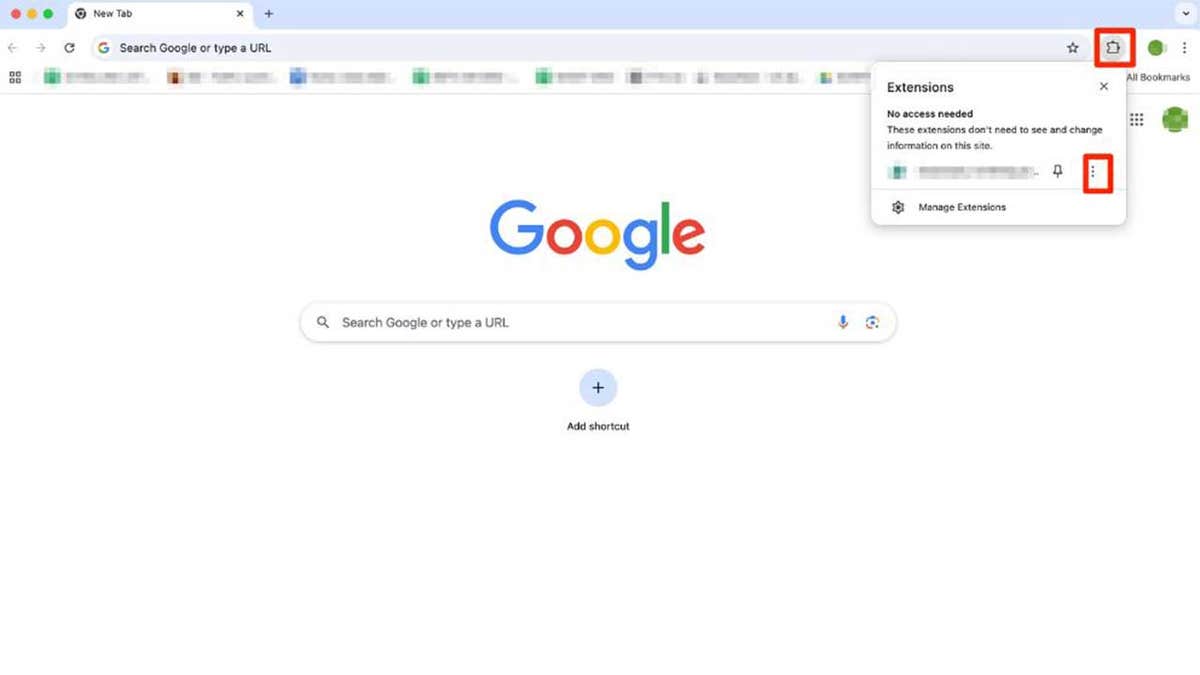
Steps to eliminate a Google Chrome extension. (Kurt “Cyberguy” Knutsson)
How to delete your private Internet data
5 ways to stay safe from incomplete extensions
If you are concerned about the previous extensions, here are five ways to safeguard your confidential information and maintain your online privacy.
1) Keep your updated browser: Chrome receives regular updates that eliminate most security problems. Be sure to activate automatic updates for your browser (for example, Chrome, Firefox, Edge) so that you are always executing the latest version without thinking about it. See my guide in Keep your devices and applications updated For more information.
2) Install extensions only from sources of trust: Official browse stores such as the Chrome website have rules and scans to catch the bad actors. They are not perfect, but they are still a better option compared to a random website on the Internet. Unknown websites extensions or third -party downloads are much more likely to hide malware or spyware.
3) Have a strong antivirus software: A good antivirus can warn you before installing malicious software, such as incomplete browser extensions. You can also alert it to the PHISHING emails and ransomware scams, helping to keep your personal information and digital assets safe. Get my elections from the best antivirus protection winners 2025 for your Windows, Mac, Android and iOS devices.
4) Be skeptical of extensions that request unnecessary access: Some extensions overreach on purpose. A calculator tool requesting its navigation history or a weather application that wants its login data is a large red flag.
Before installing, ask: “Does this permission coincide with the work of the extension?” If the answer is no, do not install it. Be careful with broad permits such as “Read and change all your data on the websites that visit” unless it is clearly justified (for example, a password administrator). If an update suddenly adds new permission requests, excave why. It could mean that the extension has been sold or pirate.
5) Change your passwords and do it safely: If you have ever saved passwords in your browser (for example, through the built -in password of Chrome or the “save password” message), those credentials could be at risk if a malicious extension was installed. These built -in managers store passwords locally or in their Google, Microsoft or Firefox account, and a committed browser can give a form of bad actors.
This generally does not apply to the dedicated extensions Password administrator, which encrypts their data independently and does not rely on the storage of the browser. However, if you are not sure if an extension has been compromised, it is always intelligent to update your master password and enable two factors.
To obtain maximum security, change your most important passwords (email, bank, purchases, cloud services) from a different and safe device, such as your phone or other computer, where the questionable extension was never installed. Avoid using the same browser that may have been exposed. Then consider changing a password administrator to create and store strong and unique session latest in the future. I have reviewed the best options in me Best password administrators of the 2025 guide. See which one best fits your needs.
Kurt key takeway
The fact that several of these extensions brought Google’s own “outstanding” badge should serve as a call for attention. He points out a serious span in the supervision and raises concerns about how exhaustive the Chrome extension review process is really. When millions of users without knowing it install Spyware under the impression that it has been examined and approved, the problem is no longer bad actors. It reflects a deeper failure within the platform itself. Google needs to assume greater responsibility improving transparency and hardening its review standards.
Do you think browsers like Google should be responsible for what is published in their stores? Get us knowing in Cyberguy.com/contact
To obtain more technological tips and safety alerts, subscribe to my free Cyberguy Report newsletter when you head Cyberguy.com/newsletter
Ask Kurt a question or let us know what stories we would like to cover.
Follow Kurt in his social channels:
Answers to the most informed Cyberguys questions:
New Kurt:
Copyright 2025 Cyberguy.com. All rights reserved.
Reference: Read Latest News in Spanish


