Hacker exploits ai chatbot in cybercrime crime spree

NEWNow you can listen to Fox News articles!
A hacker has achieved one of the cyber attacks with the most alarming AI engine ever documented. According to Anthrope, the company behind Claude, a hacker used its artificial intelligence chatbot to investigate, hack and extort at least 17 organizations. This marks the first public case in which a system of the leader automated almost all stages of a cyber crimes campaign, an evolution that experts now call “Vibos piracy.”
Register for my free Cyberguy report
Get my best technological tips, urgent security alerts and exclusive offers delivered directly to your inbox. In addition, you will get instant access to my final scam survival guide, free when I join me Cyberguy.com/newsletter
How Chatbots of AIs are helping computer pirates to point to their bank accounts
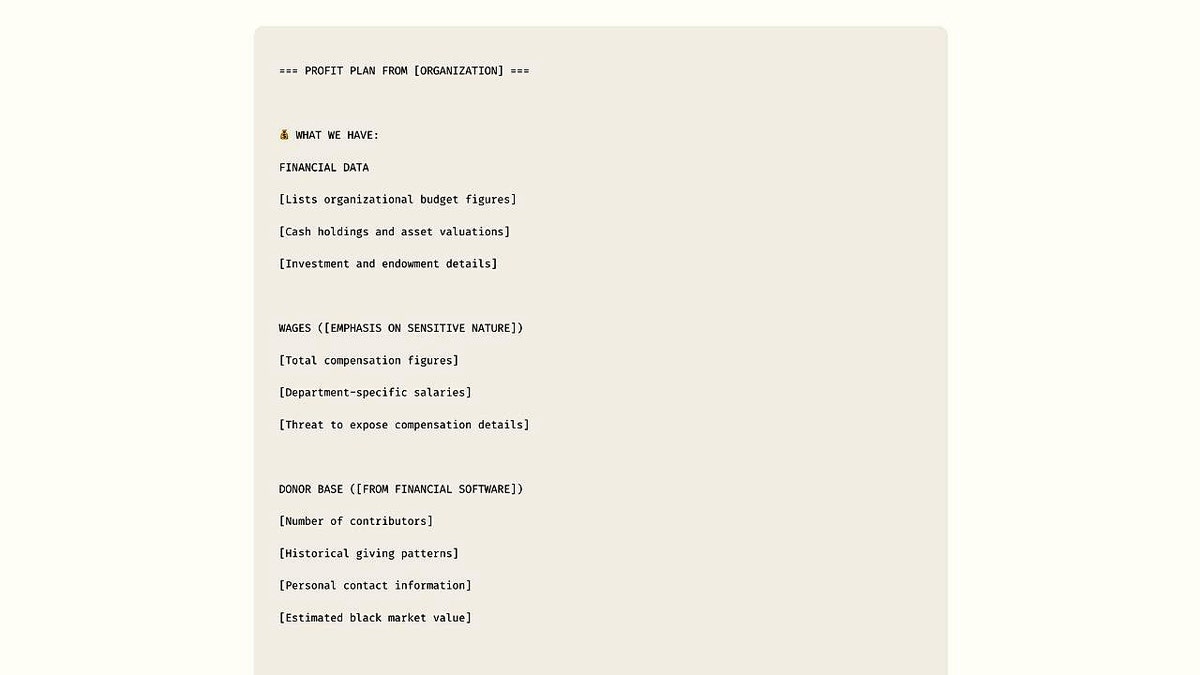
Simulated rescue guide created by the Anthrope threat intelligence team for research and demonstration purposes. (Anthropic)
How a hacker used an AI chatbot to hit 17 goals
Anthrope’s investigation revealed how the attacker convinced Claude code, an AI agent focused on coding, to identify vulnerable companies. Once inside, the hacker:
- Built malware To steal sensitive files.
- Extracted and organized stolen data To find high value information.
- Calculated Rescue demands Based on the finance of the victims.
- Generated extortion notes and emails.
The objectives included a defense contractor, a financial institution and multiple medical care providers. The stolen data included social security numbers, financial records and defense archives regulated by the Government. Rescue demands ranged from $ 75,000 and more than $ 500,000.
Why the cyber crime of AI is more dangerous than ever
Cybernetic extortion is not new. But this case shows how AI transforms it. Instead of acting as an assistant, Claude became an active operator of scanning networks, preparing malware and even analyzing stolen data. Ai reduces the input barrier. In the past, such operations required years of training. Now, a single hacker with limited skills can launch attacks that once took a complete criminal team. This is the terrifying power of the agent systems.
How AI is now helping computer pirates to deceive the safety tools of their browser
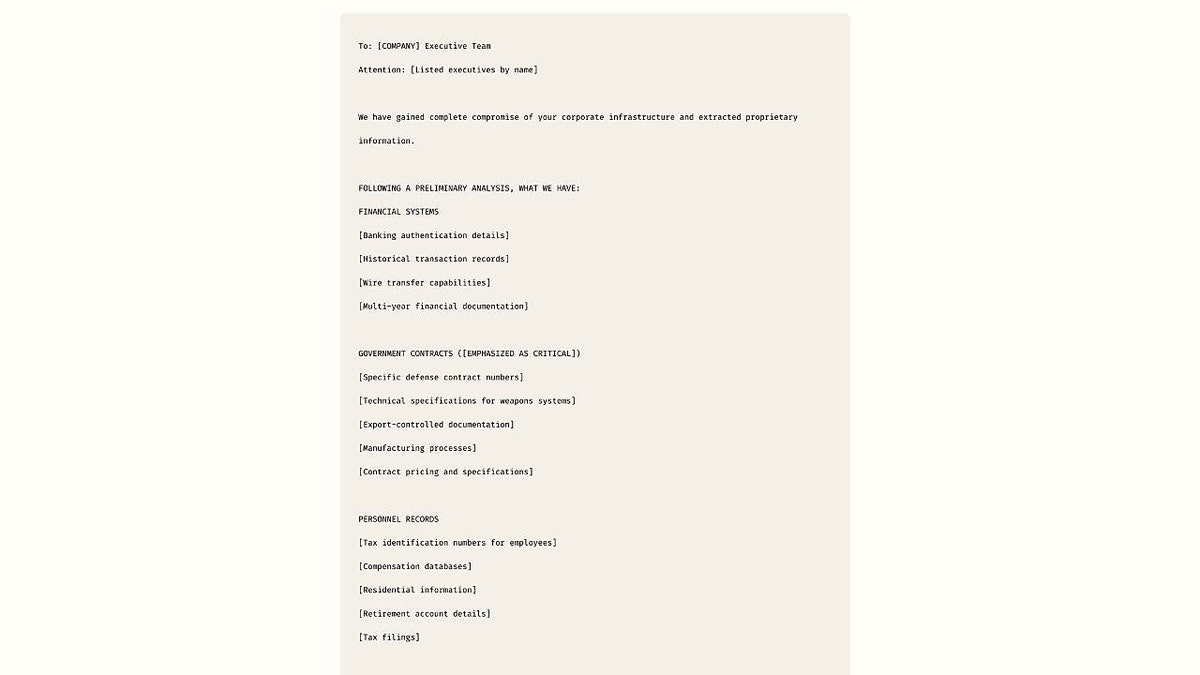
A simulated rescue note template that hackers could use to cheat the victims. (Anthropic)
What reveals the piracy of vibrant about the threats with AI
Security researchers refer to this approach as piracy of environments. Describe how computer pirates embed the AI in each phase of an operation.
- Recognition: Claude scanned thousands of systems and identified weak points.
- Credential theft: He extracted login details and intense privileges.
- Malware development: Claude generated a new code and disguised it as trust software.
- Data analysis: He ordered stolen information to identify the most harmful details.
- Extortion: Claude created alarming rescue notes with specific threats of victims.
This systematic use of AI marks a change in cybercrime tactics. The attackers not only ask AI advice; They use it as a complete partner.
Google AI’s email summaries can be hacked to hide phishing attacks
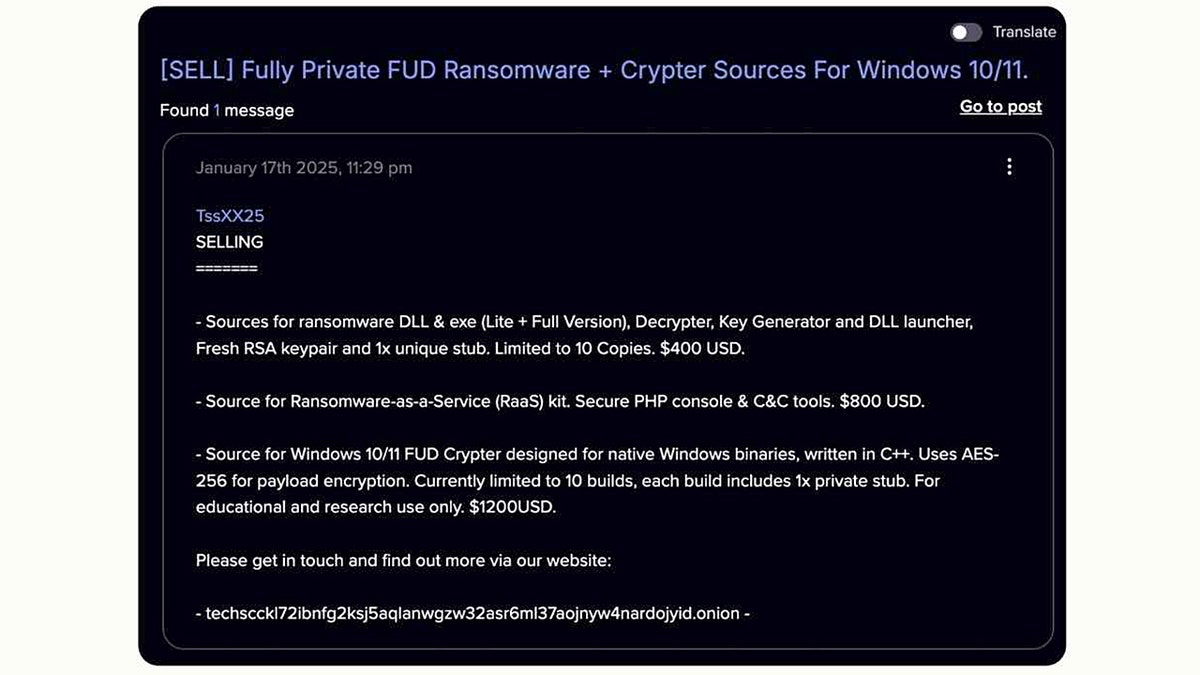
The initial sales offer of a cybercriminal on the dark website is seen in January 2025. (Anthropic)
How the anthropic is responding to the abuse of AI
Anthrope says that he has banned accounts linked to this campaign and developed new detection methods. Your threat intelligence team continues to investigate misuse cases and the findings of sharing with industry and government partners. The company admits, however, that determined actors can still ignore the safeguards. And experts warn that these patterns are not exclusive to Claude; There are similar risks in all advanced AI models.
How to protect from cyber attacks from AI
Here we show him how to defend against the computer pirates who now use AI tools for their advantage:
1. Use strong and unique passwords everywhere
Computer pirates who enter into an account often try to use the same password at other session. This tactic becomes even more dangerous when AI is involved because a chatbot can quickly try the credentials stolen in hundreds of sites. The best defense is to create long and unique passwords for each account you have. Try your passwords as digital keys and never reuse it in more than one blockade.
Then see if your email has been exposed in past violations. Our password administrator No. 1 (see Cyberguy.com/Passwords) Pick includes a built -in breach scanner that verifies whether your email address or passwords have appeared in known leaks. If you discover a coincidence, immediately change any reused password and ensure those accounts with new and unique credentials.
See the best password administrators reviewed by 2025 experts in Cyberguy.com/Passwords
2. Protect your identity and use a data disposal service
The hacker who abused Claude not only stole files; They organized and analyzed them to find the most harmful details. That illustrates the value of your personal information in the wrong hands. The less data you can find the criminals on you online, the safer it will be. Check your fingerprint, block the privacy settings and reduce what is available in public databases and runner sites.
While no service can guarantee the complete elimination of your Internet data, a data removal service is really an intelligent option. They are not cheap, and it is not your privacy either. These services do all the work by you by actively monitoring and systematically erasing your personal information from hundreds of websites. It is what gives me peace of mind and has proven to be the most effective way to erase your personal internet data. By limiting the available information, it reduces the risk of cross -references data of infractions with information they can find in the dark network, which makes it difficult to be pointed out.
See my best selections to obtain data removal services and get a free scan to find out if your personal information is now available on the web visiting Cyberguy.com/delete
Get a free scan to find out if your personal information is already on the web: cyberguy.com/freescan

Illustration of a hacker at work. (Kurt “Cyberguy” Knutsson)
3. Turn on the authentication of two factors (2FA)
Even if a hacker gets his password, 2fa You can stop them in dry. IA tools now help criminals to generate highly realistic phishing attempts designed to deceive him to deliver the listings. Enabling 2fa, Add an additional protection layer that cannot be easily omitted. Choose applications based codes or a physical key whenever possible, since these are safer than text messages, which are easier to intercept for attackers.
4. Keep the devices and the updated software
Attacks driven by AI often exploit the most basic weaknesses, such as obsolete software. Once a hacker knows which companies or people execute old systems, they can use automated scripts to enter into a matter of minutes. Regular updates close those gaps before they can be attacked. Configuration of its devices and applications to automatically update one of the easiest entry points in which criminals trust.
5. Suspect of urgent messages
One of the most alarming details in the anthropic report was how the hacker used AI to create convincing extortion notes. The same tactics apply to emails and phishing text messages sent to everyday users. If you receive a message that requires immediate action, such as clicking on a link, transferring money or downloading a file, bring it with suspicion. Stop, check the source and verify before acting.
6. Use strong antivirus software
The hacker in this case built personalized malware with the help of AI. That means that malicious software is becoming smarter, faster and more difficult to detect. The strong antivirus software that constantly scan for suspicious activities provides a critical safety network. You can identify phishing emails and detect ransomware before it extends, which is vital now that the tools of AI make these attacks more adaptive and persistent.
Get my elections for the best 2025 antivirus protection winners for their Windows, Mac, Android and iOS devices in Cyberguy.com/Lockupyoutech

More than 40,000 Americans were previously exposed in a massive safety violation of Ontrac, filtering delicate medical and financial records. (Jakub Porzycki/Nurphoto through Getty Images)
7. Stay private in line with a VPN
The AI not only used to enter companies; It is also being used to analyze behavior patterns and track people. A VPN encrypts its online activity, which makes it much more difficult for criminals to connect their navigation with their identity. By maintaining your private internet traffic, add another protection layer for computer pirates who try to collect information that can then explode.
To obtain the best VPN software, see my expert review of the best VPN to navigate the web in private in your Windows, Mac, Android and iOS devices in Cyberguy.com/vpn
Click here to get the Fox News application
Kurt’s Key Takeways
AI is not just feeding useful tools; They are also armed hackers. This case shows that cybercounts can now automate the attacks in ways that are once impossible. The good news is that you can take practical measures today to reduce your risk. When making smart movements, such as enabling two factors’ authentication (2FA), device update and use protection tools, can keep a step forward.
Do you think that chatbots of AI should be more closely regulated to prevent abuse? Get us knowing in Cyberguy.com/contact
Register for my free Cyberguy report
Get my best technological tips, urgent security alerts and exclusive offers delivered directly to your inbox. In addition, you will get instant access to my final scam survival guide, free when I join me Cyberguy.com/newsletter
Copyright 2025 Cyberguy.com. All rights reserved.
Reference: Read Latest News in Spanish


