Phishing’s new attack uses real -time interception to avoid 2FA
Phishing attacks are everywhere, and most of us can detect obvious. Even if someone falls in love with their password, the authentication of two factors (2FA) generally adds a crucial layer of protection. But a new phishing kit that performs rounds can avoid completely using session kidnapping and interception of real -time credentials.
Known as Astaroth, this tool intercepts and manipulates traffic between its device and legitimate authentication services such as Gmail, Yahoo and Microsoft. As it takes everything in real time, it completely passes to 2FA and gives the attackers full access to their account.

Illustration of a hacker at work (Kurt “Cyberguy” Knutsson)
How Astaroth works
Astaroth is a next -level phishing kit that has scam at a completely new level. Instead of using false basic login pages such as traditional phishing kits, it functions as an intermediary between its device and the real authentication service while taking everything necessary to enter.
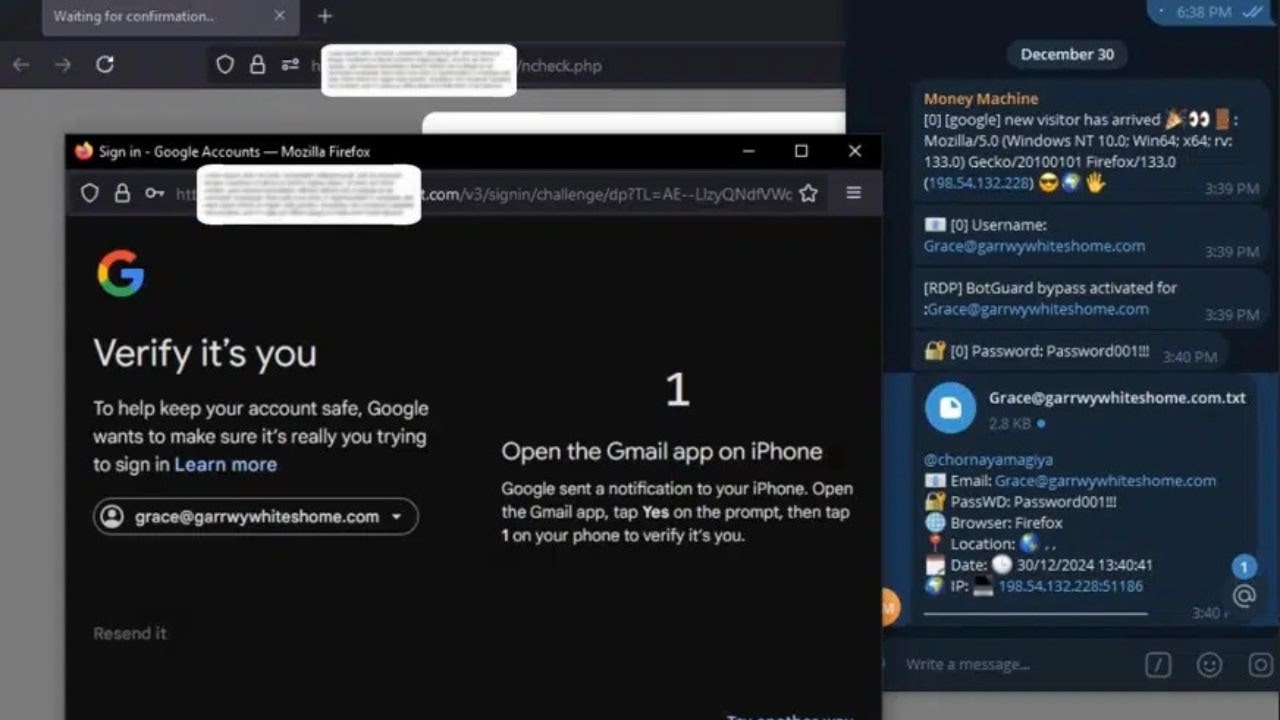
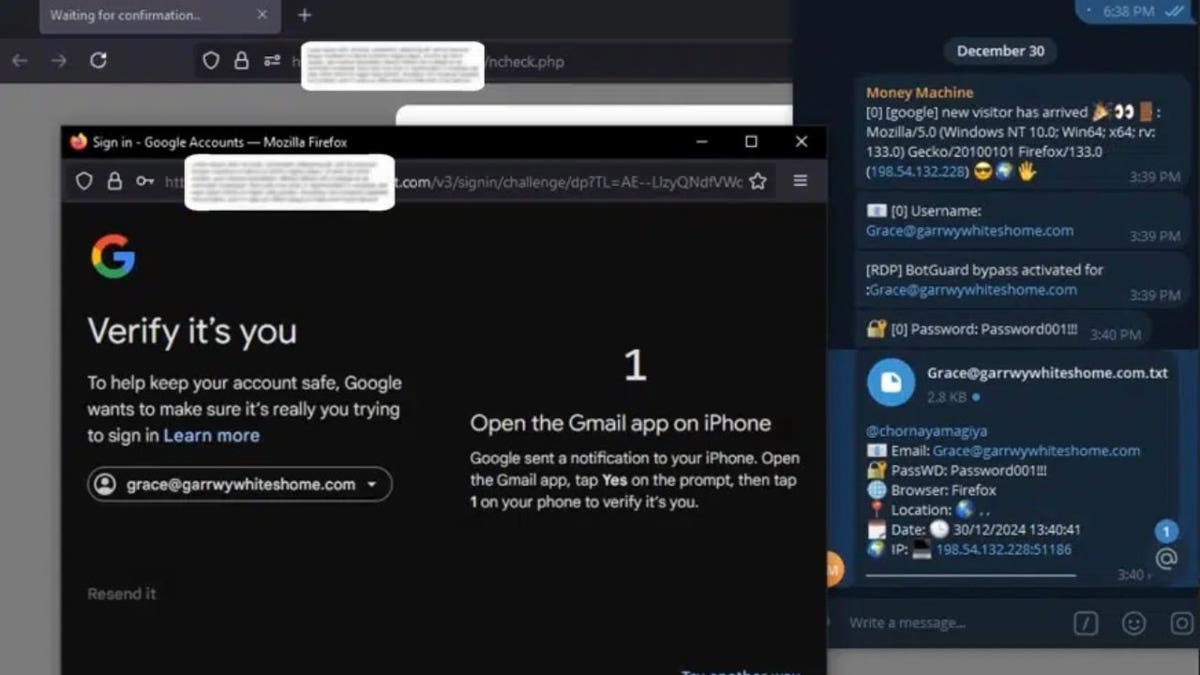
The attack begins when you click on a Phishing link and land in a malicious place that looks identical to the true. Since the site has valid SSL certificates, there are no red flags, or safety warnings or incomplete emerging windows. When you enter its login details, including username, password, device information and IP address, Astaroth snatches them before passing the application to the Real Website.
Two factors authentication It is not a problem for Astaroth. Intercepe the unique passwords in the second in which they are entered, whether they come from an application of authenticator, SMS or an push notification. The stolen codes instantly sent the attacker through a web panel or telegram alert, so that they can use them before they expire.
The real trick is that Astaroth also takes session cookies, which are the small data bits that keep registered users after authentication. The attackers can inject these cookies into their own browsers, jumping the need for passwords or authentication of two factors completely. Once they have the session, no additional steps are required.
An example of what the victim and the attacker (Slashnext) would see (Kurt “Cyberguy” Knutsson)
Best antivirus for Mac, PC, iPhones and Androids – Cyberguy Picks
Astaroth is surprisingly advanced
As reported by Cybersecury Company SlashnextAstaroth stands out from other phishing kits due to its ability to intercept credentials in real time, automate attacks and resist demolition efforts. Traditional phishing depends on deceiving the victims to enter their credentials in false login pages, but Astaroth eliminates that step completely.
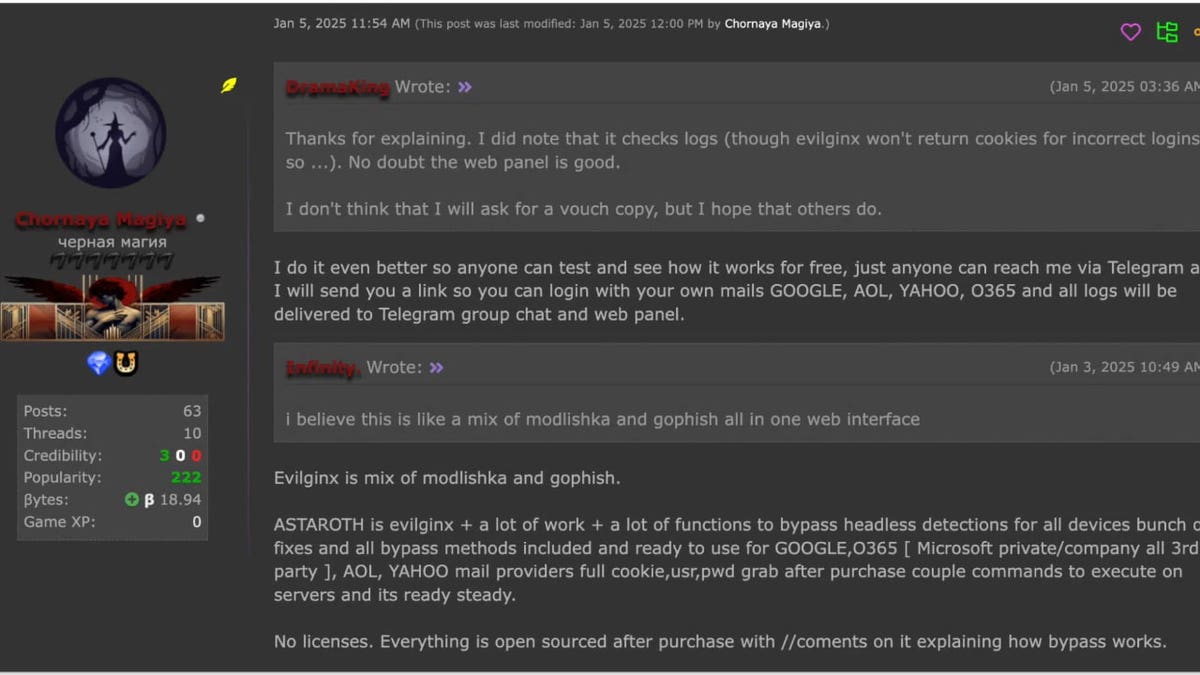
Beyond its advanced abilities, Astaroth comes with characteristics that make it attractive to cybercriminals. Use bulletproof accommodation to stay online despite the application efforts of the law, receive frequent updates to avoid safety patches and follow a structured payment model. For $ 2,000, buyers get six months of continuous updates. To generate trust, creators even let computer pirates try the Phishing kit before buying.
Astaroth is widely available through telegram and cybercrimic cybernetic forums. The anonymity of these platforms makes it difficult for the authorities to track the distribution.
The seller sharing information about the Phishing Kit test (Slashnext) (Kurt “Cyberguy” Knutsson)
How to protect your IRS scam data this tax
Signals that can be infected with Astaroth
1) Log in unexpected account or safety alerts
- Receive Gmail, Microsoft or other session services from an unknown device or location
- You receive a 2FA application when you did not try logging
2) You are mysteriously without account account
- If cookies were stolen from your session, an attacker could log in like you and force a session closure closure in another place
3) password changes or configuration updates that did not perform
- If an attacker has control, you can change the emails of recovery, telephone numbers or passwords
4) Slow performance of the odd system or behavior
- Astaroth uses legitimate Windows processes (such as WMIC, Bitsadmin or RegSVR32) to hide
- If your system is slow or the task manager shows strange processes using a high CPU/Network without explanation, that could be a track
5) The browser acts strangely
- The login fields are produced incorrectly or redirect loops
- The pages that used to work suddenly trigger warnings or errors
6) Unknown programs or scripts that are executed in the background
- Verify odd scheduled tasks, registration changes or background network connections (especially if they are going out to suspicious domains or IP).
What to do if you suspect infection
- Disconnect from the Internet immediately
- Execute a complete malware scan wearing Trusted antivirus software
- Verify the unauthorized session in its main accounts and Change all passwords In another trust device
- Enable passkeeys or hardware safety keys Where possible
- Rest your device If malware persists; A complete factory restart may be required
- Monitor bank accounts and email input trays by suspicious activity
4 ways to stay safe from Phishing’s attacks by Astaroth
1) Avoid unknown links and use strong antivirus software: Remember that it doesn’t matter how advanced malware, you still need your entry. In most cases, an attacker will require clicking on a link before you can steal your data. For example, for Astaroth to work, you must click on a link, visit a malicious website and enter its credentials. If you do not click on the link, it remains clear about malware.
The best way to safeguard the malicious links that install malware, which potentially access their private information, is to have strong antivirus software installed on all its devices. This protection can also alert it to the PHISHING Electronic Correos and Ransomware scams, maintaining their personal information and their safe digital assets. Get my elections for the best 2025 antivirus protection winners for your Windows, Mac, Android and iOS device.
2) Double verification sites: Always verify the website addresses and use markers for trusted sites. Instead of clicking links in emails or messages, manually write the URL or use a trusted marker. This minimizes the risk of landing on a fraudulent page designed to imitate a legitimate website.
3) Update its devices: You may wonder how to keep your devices updated help against malware such as Astaroth. While it does not directly avoid an attack, it ensures that the situation does not get worse. Maintain your operating system and updated applications With the latest security patches, closing vulnerabilities that malware could exploit, which makes attackers difficult to stain on their device.
4) Avoid writing passwords: Avoid entering passwords whenever possible to reduce the risk of credentials. Instead, use authentication methods such as Passkeys, Google Sign-in or Apple Sign-In.
TO master key It is a characteristic that uses pairs of cryptographic key to verify its identity, eliminating the need for traditional passwords. It allows you to log in to applications and websites using the same process you use to unlock your device, such as biometry, pin or pattern.
Google login It is a feature that allows you to log in to third -party websites or websites using your Google account credentials. Simplify the login process by eliminating the need to create and remember separate user and password names for each service. You can log in through a “Login with Google” button, a Google login message or automatic login if previously authorized.
Apple’s login It is a feature that allows you to log in private in applications and websites of participating third parties using your Apple ID. It offers a quick, easy and more deprived way to authenticate without the need to create new accounts or remember additional passwords. To configure an account for “Log in with Apple”, when a participating website or application asks you to configure or update an account, do the following: Touch log with Apple. Follow the on -screen instructions. Some applications (and websites) do not request your email name and address. In this case, it simply be authentic with Face ID or Touch ID (depending on your model), then begins to use the application. Others may request your email name and address to configure a personalized account. When an application requests this information, log in with Apple shows its name and the personal email address of your Apple account to check it.
These methods are based on cryptographic keys or safe tokens, which makes it much more difficult for attackers to intercept their login information, even if they manage to deceive it to visit a malicious site.
The FBI warns about a new scam of ‘dangerous’ smishing that goes to his phone
Kurt key takeway
Astaroth shows how far the phishing kits have arrived, carrying things beyond the usual tricks and overlooking 2fa easily. It is a reminder that no matter how safe we believe that they are our systems, there is always a smarter attack waiting to exploit the holes. Cybercriminals are adapting quickly, and although traditional defenses may not cut it anymore, there are still steps that can be taken to fight: use session initials without a password, keep updated and continue learning about these threats evolving.
What do you think governments and companies should do to protect it from sophisticated cyber threats such as Astaroth Phishing Kit, which can avoid traditional security measures? Get us knowing in Cyberguy.com/contact.
To obtain more technological tips and safety alerts, subscribe to my free Cyberguy Report newsletter when you head Cyberguy.com/newsletter.
Ask Kurt a question or let us know what stories we would like to cover.
Follow Kurt in his social channels:
Answers to the most informed Cyberguys questions:
New Kurt:
Copyright 2025 Cyberguy.com. All rights reserved.
Reference: Read Latest News in Spanish


