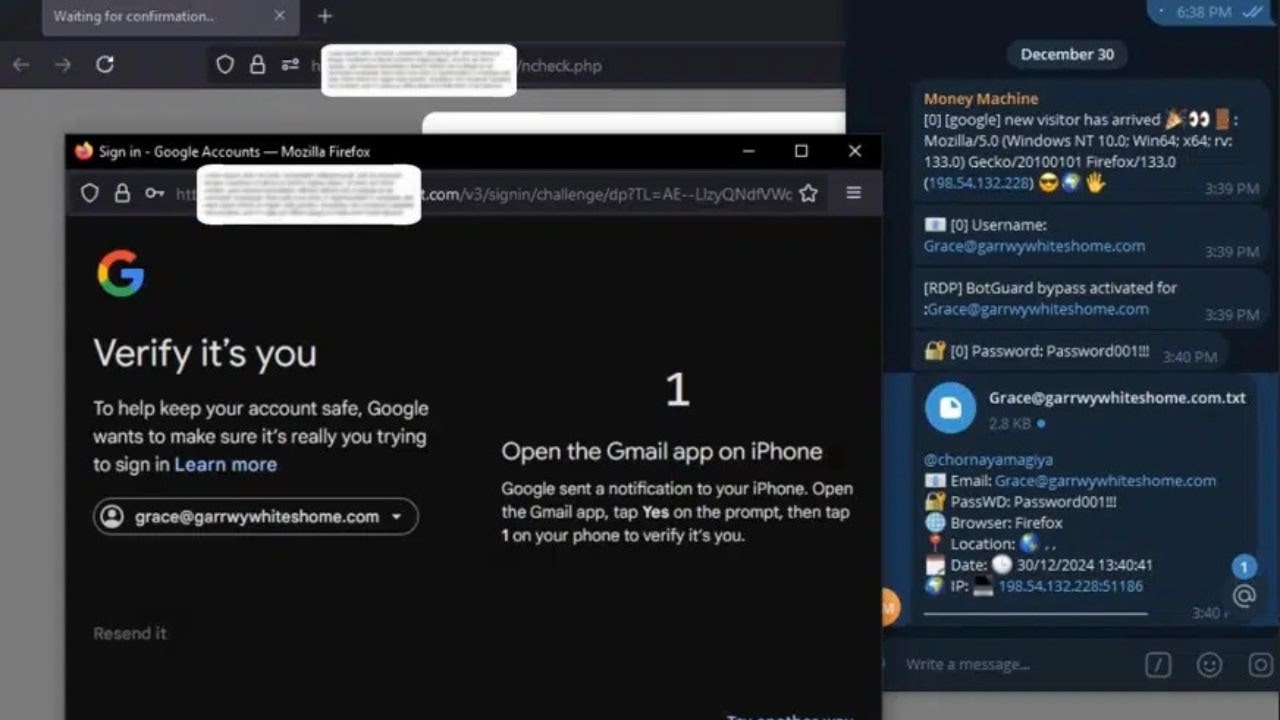
Hackers steal medical records, financial data of 1.2 million patients in massive healthcare breach
SimonMed Imaging suffered a massive ransomware attack allegedly by the Medusa group, with hackers demanding $1 million for stolen medical and financial data.